As information technology and its interconnectivity continue to push the transportation industry forward and make the underlying infrastructure more efficient, the risk of cyberattacks increases. Technology is driving innovations in aviation, roads and bridges, inland waterways, ports, rail, transit, and shipping/delivery. Automotive and Mobility as a Service (MaaS) systems have their own complexities, but there are clear steps you can take for increased cybersecurity in the transportation industry.
Other industries are facing similar challenges as more of their systems rely on cloud computing and 5G connectivity: for instance, the explosion in telehealth technology and wearable devices in the medical field. The more information we transmit through wireless networks, and the more interconnected those networks are, the more opportunities cybercriminals will have to access and exploit that information.
But when it comes to cybersecurity in the transportation industry, there’s much more than privacy and financial information at stake: the health and safety of passengers and operators as well as the vehicles, their surroundings, and any goods being transported are in physical danger when bad actors can access navigation and control systems.
Four Layers of Cybersecurity Risk
To understand these risks and create effective security strategies, we must understand the systems and data we need to protect. There are four main layers of cyber systems that open up various risks.
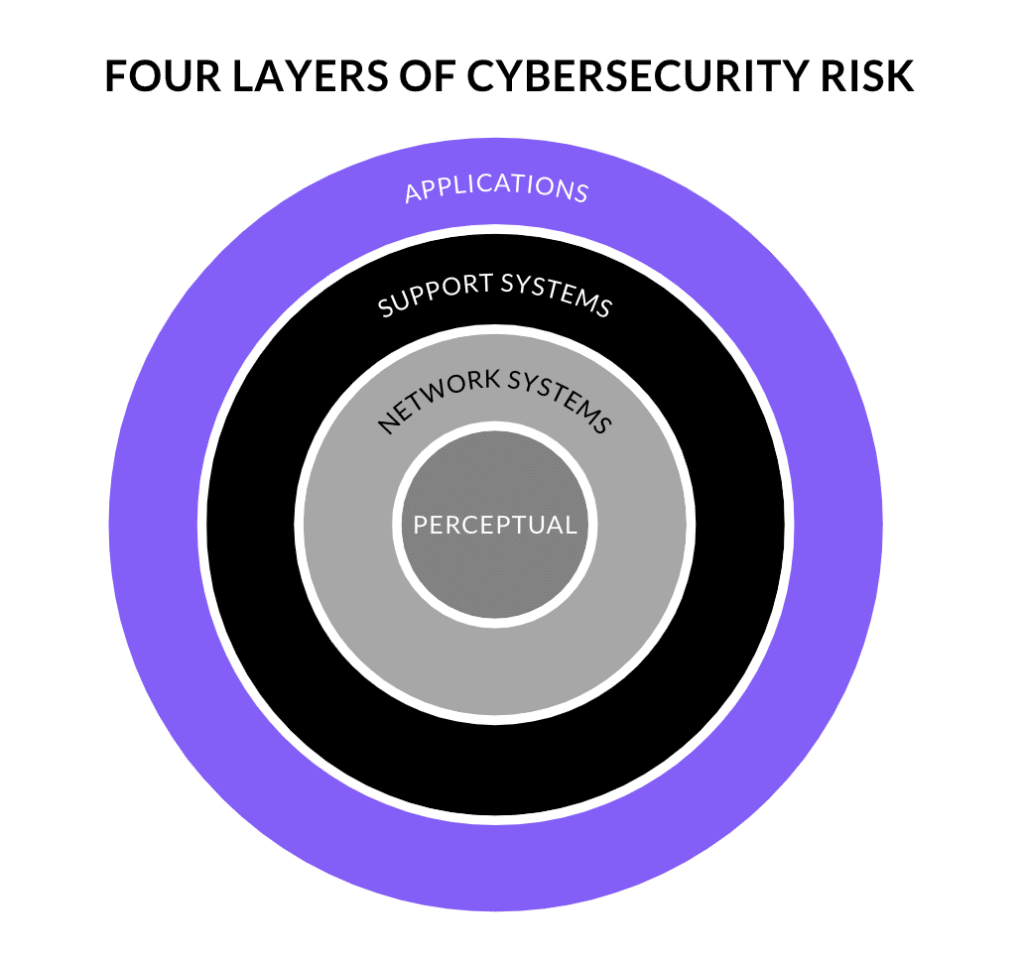
Perceptual
The first is the perceptual layer, which links the digital with the physical through sensory components like motion sensors and GPS. The fact that these links can span wide geographic areas and centralize access to hundreds of pieces of equipment multiplies the risk exponentially.
Network Systems
The second is network systems, which transmit information, such as satellite networks and mobile connectivity (5G). Transportation companies monitor everything from traffic to weather conditions and closures at ports and borders in real-time. Think about the amount of data and the processing speed it might take to keep an airport running smoothly. Each access point, from ticket kiosks to terminals, cockpits and air traffic control, needs to be monitored and protected from hackers and bots. What’s worse, one disruption in that system can bring down the other components around it, causing widespread delays, confusion and even theft of cargo.
Support Systems
The third layer is support systems, such as cloud computing and artificial intelligence. Some of the data stolen in reported cyberattacks has included intellectual property and trade secrets. Shipping companies have also started to store tracking information in the cloud for customers to access at their convenience. These components are vulnerable to ransomware attacks; blocking access to cloud data and artificial neural networks can effectively shut down an entire system.
Applications
The final layer is made up of applications, which link users with goods, services, and transportation in the physical world. Compromised ticketing and scheduling systems can shut down transportation hubs for hours or days, which has happened with rail systems and airports around the world. Of course, any system that stores credit card information is susceptible to theft of that private data.
Transportation’s Biggest Risk
Currently, the biggest risk for cybersecurity in the transportation industry are companies digitizing their services is unauthorized access to data. Based on the layers of data we’ve covered here, it’s clear that this encompasses a wide range of data types and potential effects. Because most transportation companies combine legacy technologies (most of which were not designed with security systems) with newer components, the connections between these networks make their data especially vulnerable.
Malicious data breaches account for 27.1 percent of all incidents, resulting in an average loss of $330,000 per episode. However, of all of the types of cyber incidents, unintentional disclosure of data is the most destructive, costing victim companies on average $3.17 million per occurrence.
Customized Security Solutions
Each transportation system requires custom-built security solutions that protect each type of data they store and transmit as well as every endpoint. Effective strategies may include a combination of firewalls, software encryption, virus detection, system compartmentalization, and other techniques with live monitoring and a comprehensive incident response plan.
Any time changes are made to your company’s data infrastructure, security should be a big consideration in your implementation plan. Get in touch with us today to make sure your future is secure and you’re well equipped with the best cybersecurity in the transportation industry.
Additional Resources
https://www.isacybersecurity.com/cybersecurity-for-the-transportation-sector/

